Energy-efficient bcrypt cracking
These are the slides we used at
PasswordsCon Las Vegas 2014 (colocated with BSidesLV),
Skytalks 2014 (colocated with DEFCON), and
FSEC 2014.
We used
a much older version of these slides at
PasswordsCon Bergen 2013.
Please click on the slides for higher-resolution versions.
You can also
download a PDF file with all of the slides (7.4 MB) and
watch a video of the talk (YouTube).
We also used a
summary version
(2.6 MB) of these slides at
USENIX WOOT '14,
and we recommend that you read our WOOT '14
paper (268 KB, 7 pages).
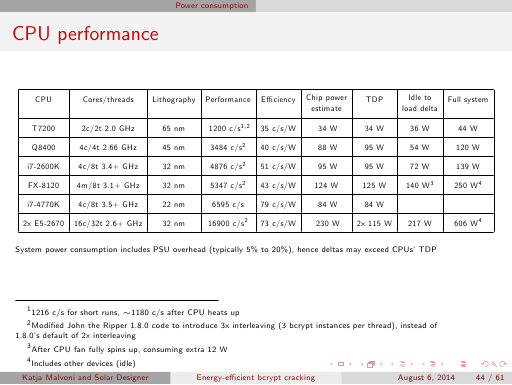
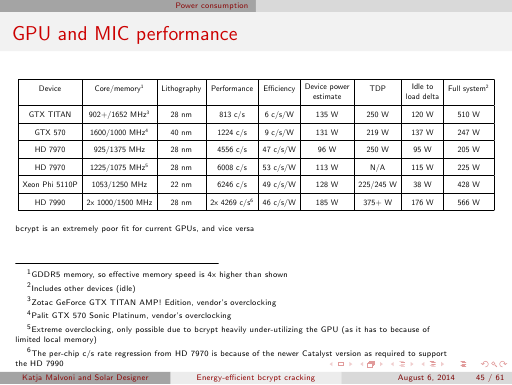
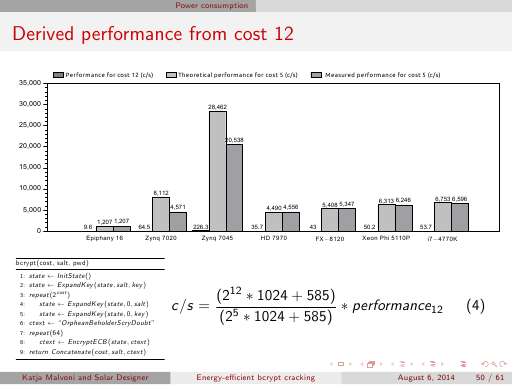
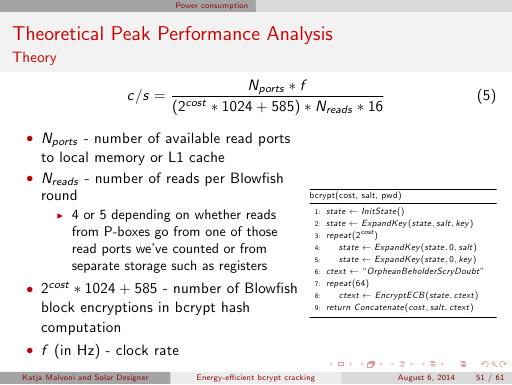
Errata: the number 1024 used in formulas on slides 50 and 51 (slide 15 in the summary version) and on pages 4 to 6 in the paper
should actually be 1042 (as (512+9)*2). Correcting it would very slightly affect our reported theoretical and derived speeds.
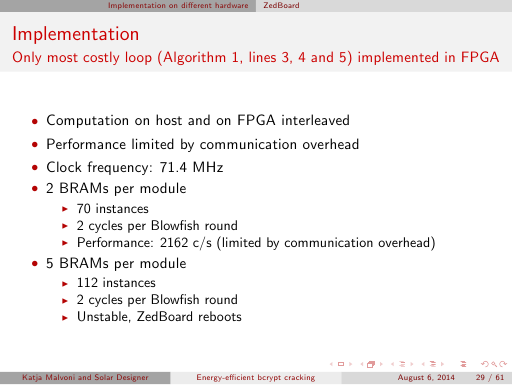
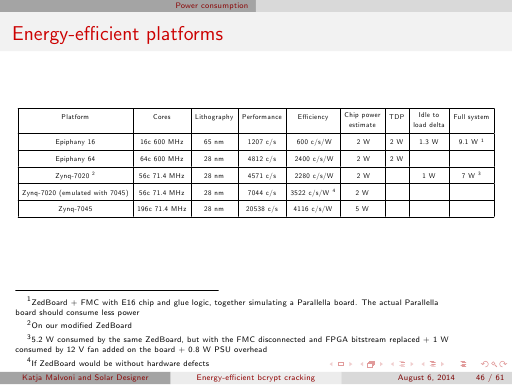
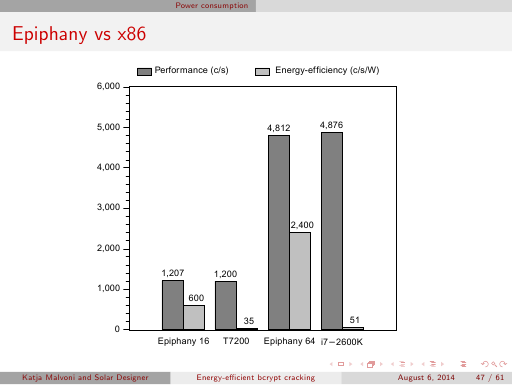
Update: the most optimized implementation described on slide 33 and in the paper on pages 3 and 4,
which was unstable on our ZedBoard despite of hardware modifications, became stable on a newer ZedBoard revision without any
custom hardware modifications, actually delivering on the Zynq 7020 the same speed of over 7000 c/s at bcrypt cost 5 that we had
achieved by emulation on a Zynq 7045 board.
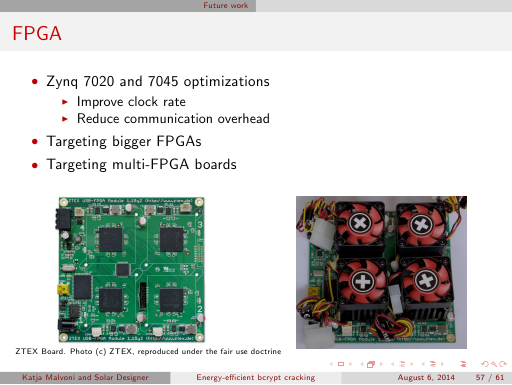
Update: we've since
implemented bcrypt on ZTEX 1.15y quad-FPGA boards
(which was mentioned as part of "Future work" on slide 57 here), achieving much higher speeds than anything shown here
(eventually 119k c/s at bcrypt cost 5 per board,
over 1.6M c/s for an older revision on a 16-board cluster managed from one Raspberry Pi,
2.1M c/s on 18 boards in a production rig consuming 585 Watts, and four times that for the four rigs assembled).
We've also
implemented a number of other hash types on those boards,
with support for all of that merged into John the Ripper bleeding-jumbo branch and
1.9.0-jumbo-1 release, thus available for actual use (not just research).




100240





























































